Fully Managed Vault just for €9
Fully Managed Vault just for €9
Fully Managed
Vault
just for €9
Fully Managed
Vault
just for €9
Free 7 day trial - no credit card needed
Vault is the Enterprise-Grade Secret Management Platform That Transforms Cybersecurity from a Reactive Challenge to a Proactive Strategic Advantage, Providing Unparalleled Protection for Your Most Critical Digital Assets
Vault is the Enterprise-Grade Secret Management Platform That Transforms Cybersecurity from a Reactive Challenge to a Proactive Strategic Advantage, Providing Unparalleled Protection for Your Most Critical Digital Assets
You can relax knowing that we are taking care of Encryption, Security, Installations,
Updates, Migrations, Monitoring, Upgrades, Scalability, Customizations, DNS, SMTP & Backups
You can relax knowing that we are taking care of Encryption, Security, Installations, Updates, Migrations, Monitoring, Upgrades, Scalability, Customizations, DNS, SMTP & Backups

Secure, Fast & Scalable
Fully
Managed
We handle the entire hosting lifecycle. From initial launch to system tuning, we manage the technical details so you can focus entirely on using the software.
Proactive
Protection
With cyber threats on the rise, we take security seriously. From active server monitoring to custom firewalls. We block bots and malicious traffic before they reach your data.
Guaranteed
Performance
Downtime hurts. We monitor uptime & performance around the clock. Our scalable infrastructure ensures your applications remain fast and responsive, even as your data grows.
Automated
Updates & Backups
We monitor releases and apply security patches and updates automatically. We run daily off-site backups, allowing one-click recovery to ensure your data remains safe.
Secure, Fast & Scalable
Fully
Managed
We handle the entire hosting lifecycle. From initial launch to system tuning, we manage the technical details so you can focus entirely on using the software.
Proactive
Protection
With cyber threats on the rise, we take security seriously. From active server monitoring to custom firewalls. We block bots and malicious traffic before they reach your data.
Guaranteed
Performance
Downtime hurts. We monitor uptime & performance around the clock. Our scalable infrastructure ensures your applications remain fast and responsive, even as your data grows.
Automated
Updates & Backups
We monitor releases and apply security patches and updates automatically. We run daily off-site backups, allowing one-click recovery to ensure your data remains safe.
Vault features & resources
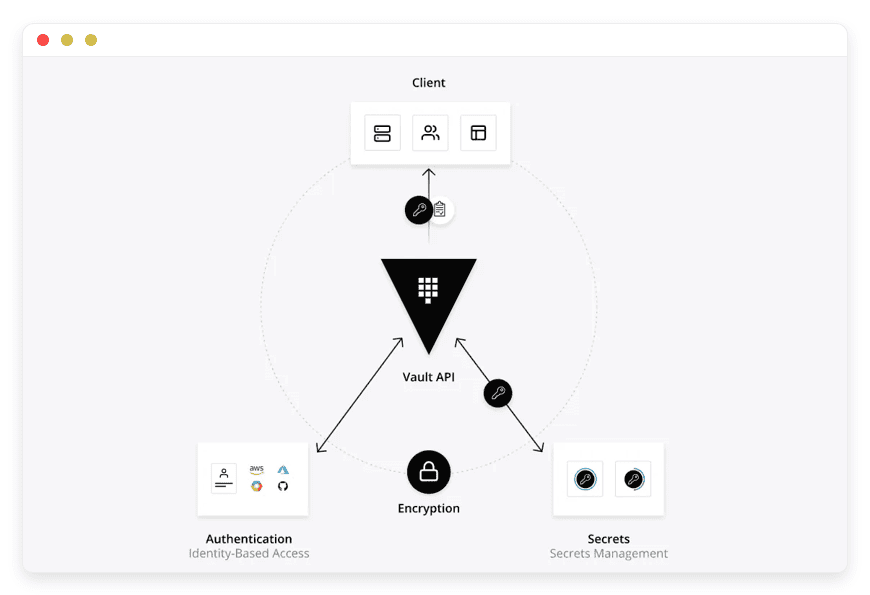
Dynamic Secrets Generation
Dynamic Secrets Generation
Revolutionize credential management by generating short-lived, automatically rotating secrets that dramatically reduce the risk of credential compromise. Eliminate static, long-lived credentials that become potential security vulnerabilities over time. Create a dynamic ecosystem where credentials are generated on-demand and automatically expire, ensuring maximum security with minimal administrative overhead. Implement fine-grained access controls that provide precise management of secret lifecycles. Transform secret management from a static defense to an adaptive, intelligent security strategy.
Universal Secret Encryption
Universal Secret Encryption
Provide a comprehensive encryption solution that protects sensitive data across your entire digital infrastructure. Encrypt, store, and tightly control access to tokens, passwords, certificates, API keys, and other critical secrets with military-grade encryption mechanisms. Create a centralized vault that serves as the single source of truth for all sensitive organizational credentials. Implement robust access policies that ensure only authorized systems and personnel can retrieve or modify protected secrets. Build a foundational security layer that adapts to complex enterprise environments.
Advanced Authentication Mechanisms
Advanced Authentication Mechanisms
Develop a sophisticated authentication ecosystem that goes beyond traditional access control methods. Support multiple authentication strategies including multi-factor authentication, cloud provider integrations, and complex role-based access controls. Create granular permission structures that allow precise control over who can access specific secrets under specific conditions. Integrate seamlessly with existing identity providers and enterprise authentication systems. Eliminate the complexity of managing diverse authentication requirements across different platforms and environments.
Comprehensive Audit Logging
Comprehensive Audit Logging
Transform secret management into a transparent, fully traceable process with advanced audit and compliance capabilities. Generate detailed, immutable logs that capture every interaction with secrets, providing complete visibility into access patterns and potential security events. Enable forensic-level tracking that supports compliance requirements and helps detect potential security anomalies in real-time. Create a robust accountability framework that allows instant investigation of any secret-related activity. Provide security teams with the insights needed to proactively manage and mitigate potential risks.
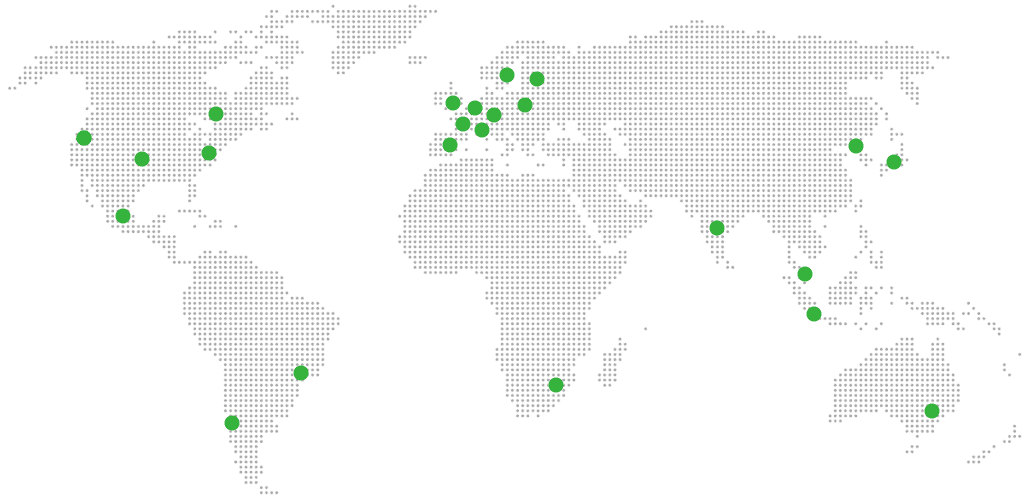
Global Reach
Global Reach
21 worldwide locations
21 worldwide locations
Activate & use any Software near you
Activate & use any Software near you
United States, Germany, Finland, Singapore, Australia, Brazil, Canada, Netherlands, UK, Spain, Italy, France, Sweden, Malaysia, India, Japan, Mexico, Poland, South Korea, Chile, South Africa and more coming soon
United States, Germany, Finland, Singapore, Australia, Brazil, Canada, Netherlands, UK, Spain, Italy, France, Sweden, Malaysia, India, Japan, Mexico, Poland, South Korea, Chile, South Africa and more coming soon
🇺🇸°🇩🇪°🇫🇮°🇸🇬°🇧🇷°🇦🇺°🇬🇧°🇪🇸°🇸🇪°🇲🇾°🇨🇦
🇳🇱°🇿🇦°🇮🇹°🇫🇷°🇵🇱°🇲🇽°🇯🇵°🇮🇳°🇰🇷°🇨🇱
🇺🇸°🇩🇪°🇫🇮°🇸🇬°🇧🇷°🇦🇺°🇬🇧
🇪🇸°🇸🇪°🇲🇾°🇨🇦°🇳🇱°🇿🇦°🇮🇹
🇫🇷°🇵🇱°🇲🇽°🇯🇵°🇮🇳°🇰🇷°🇨🇱
Frequently Asked Questions
Frequently Asked Questions
Here are some most commonly asked questions